From IMDSv1 detection to IMDSv2 enforcement
AWS Instance Metadata Service Version 2: Transforming Cloud Security Through Enhanced Authentication
The AWS Instance Metadata Service Version 2 (IMDSv2) represents a critical evolution in cloud security architecture, fundamentally addressing vulnerabilities that have plagued cloud environments since the inception of the original metadata service. This comprehensive analysis examines how IMDSv2’s session-oriented authentication model has transformed the security landscape, providing robust protection against Server-Side Request Forgery (SSRF) attacks and other exploitation vectors that previously enabled significant data breaches, including the notorious Capital One incident of 2019.
Introduction to Instance Metadata Service
Understanding the AWS Instance Metadata Service
The AWS Instance Metadata Service (IMDS) serves as a critical component of the EC2 infrastructure, providing running instances with essential information about themselves, including instance ID, AMI ID, security groups, and most importantly, IAM role credentials. This service operates on a link-local IP address (169.254.169.254) that is accessible only from within the EC2 instance itself, making it a foundational element for cloud-native applications that require runtime configuration and credential access.
Since its introduction over a decade ago, IMDS has solved a fundamental challenge in cloud computing by eliminating the need to hardcode or manually distribute sensitive credentials to instances. Applications running on EC2 instances can dynamically retrieve temporary, frequently-rotated credentials without requiring external API calls or static configuration files. This approach has become essential for modern cloud architectures, where security best practices mandate the use of temporary credentials over long-lived access keys.
The Security Challenge of IMDSv1
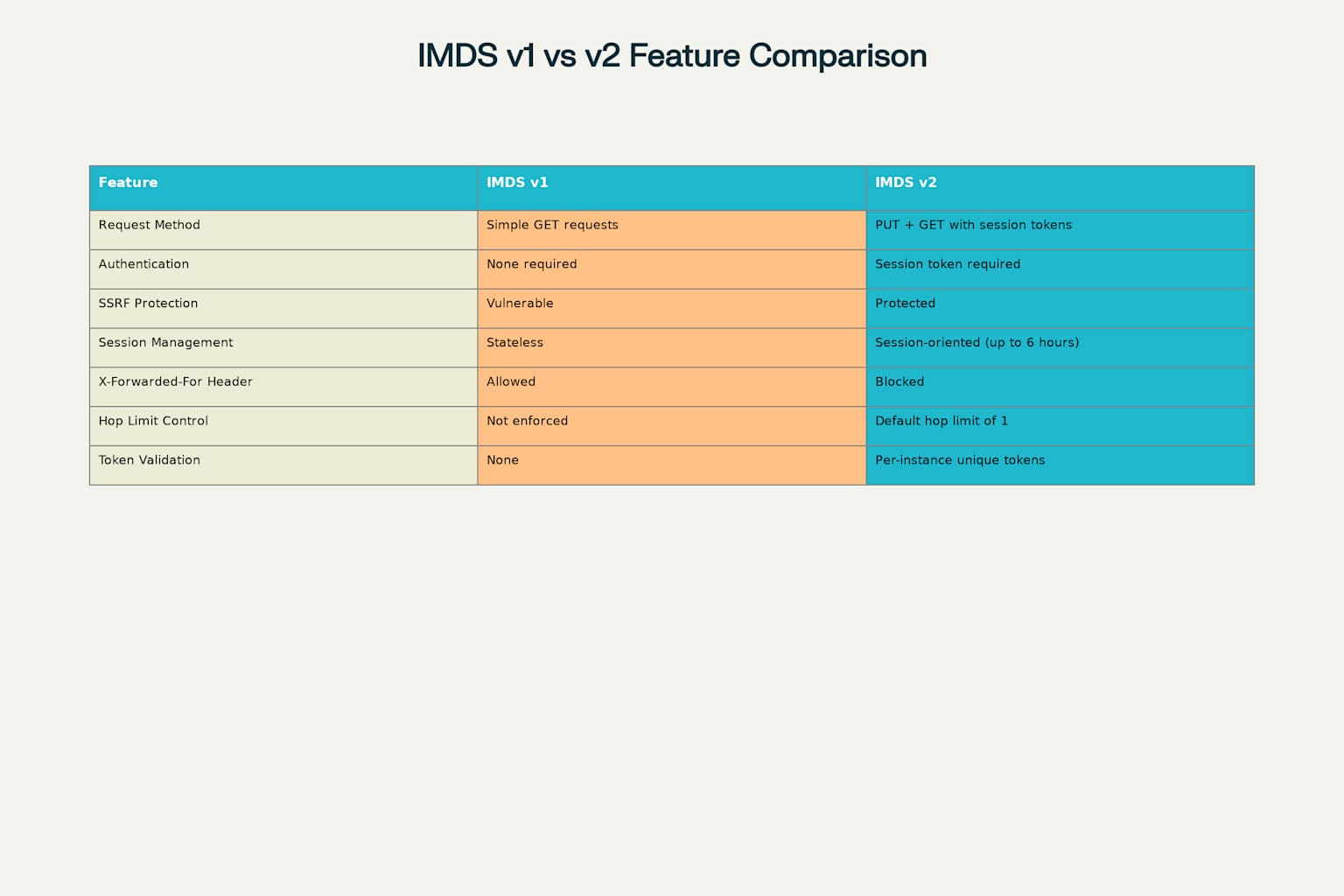
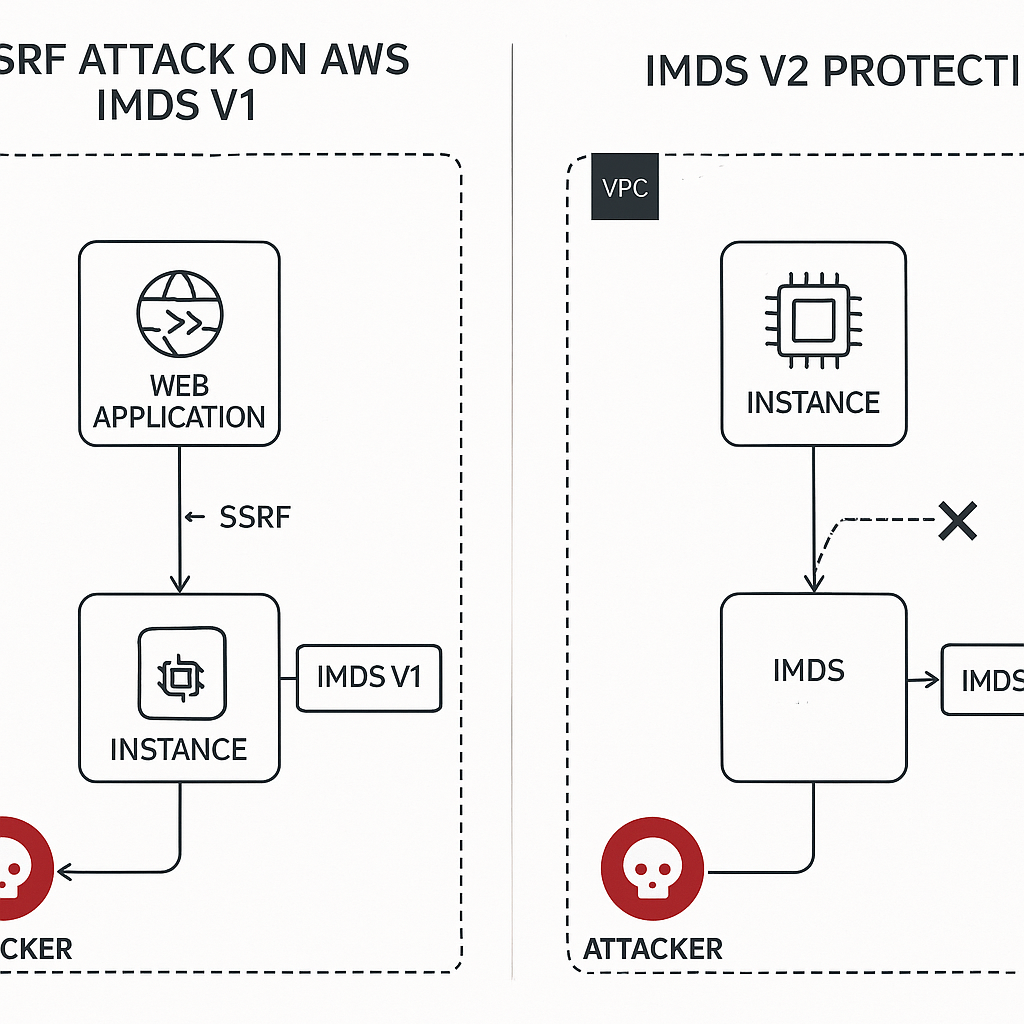
The original Instance Metadata Service (IMDSv1) utilized a simple request-response protocol based on standard HTTP GET requests. While functionally effective, this design created significant security vulnerabilities that attackers could exploit through various vectors. The most prominent of these vulnerabilities was susceptibility to Server-Side Request Forgery (SSRF) attacks, where malicious actors could leverage web application vulnerabilities to make unauthorized requests to the metadata service.
Comparison of IMDS v1 vs IMDS v2 Security Features
The fundamental security flaw in IMDSv1 stemmed from its lack of authentication mechanisms. Any process or application capable of making HTTP requests from within an EC2 instance could access sensitive metadata, including IAM credentials, without any form of verification or authorization. This design philosophy, while convenient for developers, created an expansive attack surface that sophisticated threat actors learned to exploit systematically.
IMDSv2: A Security-First Redesign
Session-Oriented Authentication Architecture
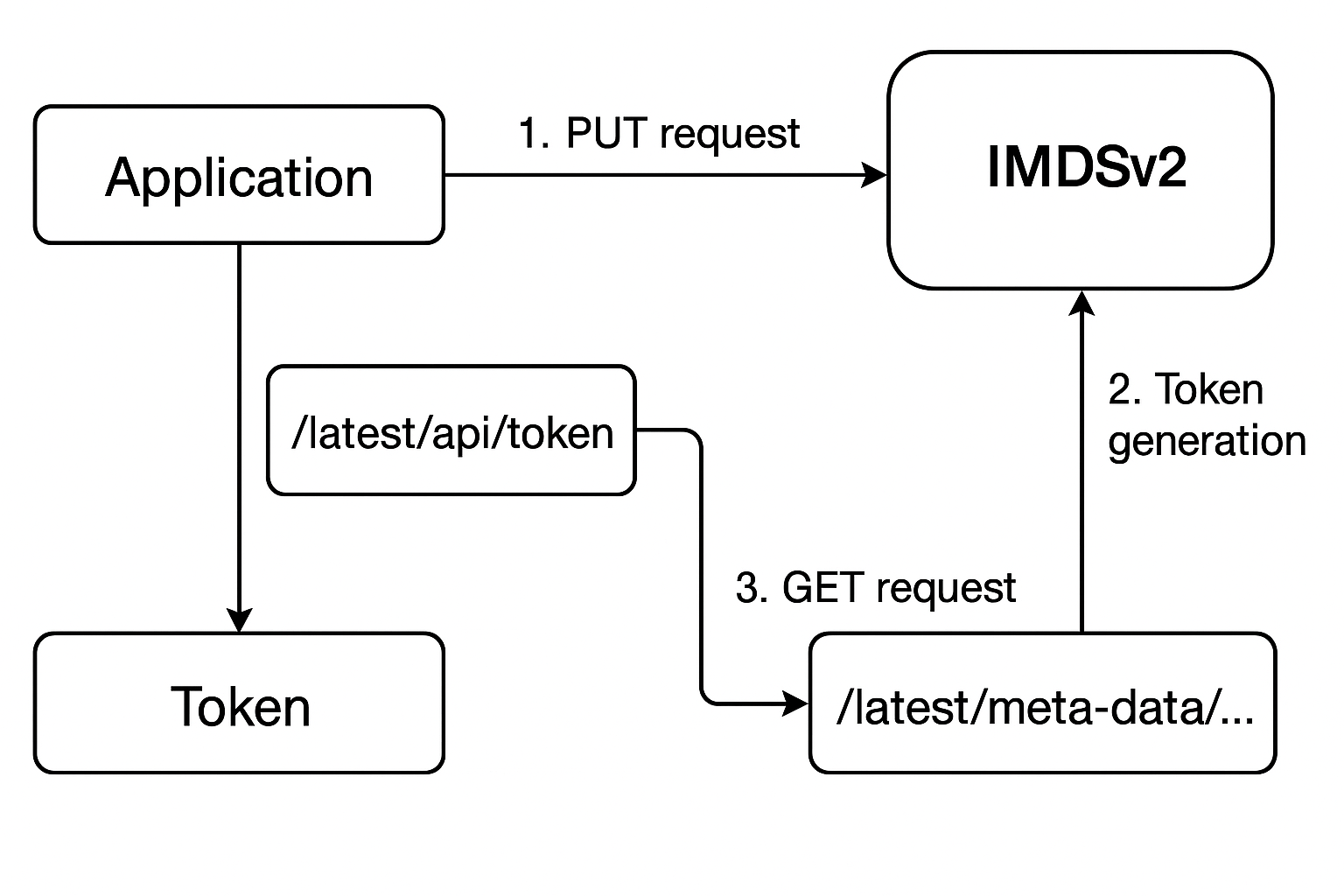
AWS introduced IMDSv2 in November 2019 as a complete reimagining of the metadata service architecture, implementing session-oriented authentication to address the fundamental security weaknesses of its predecessor. The new design requires a two-step process: first, applications must request a session token using an HTTP PUT request with specific headers, and then use this token for subsequent metadata requests.
IMDS v2 Session-Oriented Architecture and Workflow
The session token mechanism introduces several critical security enhancements. Each token is instance-specific and cannot be used on other EC2 instances, even if an attacker manages to intercept it. Sessions can be configured with a time-to-live (TTL) ranging from one second to six hours, allowing administrators to balance security with operational efficiency. The token-based approach ensures that even if an application is vulnerable to SSRF attacks, the attacker cannot easily obtain the session token required for metadata access.
Protection Against Attack Vectors
IMDSv2 implements multiple layers of protection against various attack vectors that previously threatened cloud security. The service blocks PUT requests containing X-Forwarded-For headers, preventing many proxy-based attacks. Additionally, the default hop limit of 1 ensures that metadata responses cannot travel beyond the instance itself, protecting against network-level attacks even in misconfigured environments.
SSRF Attack Flow: IMDS v1 Vulnerability vs IMDS v2 Protection
The session-oriented design specifically targets SSRF vulnerabilities, which have been responsible for numerous high-profile breaches. Most SSRF attack vectors rely on simple GET requests, making them ineffective against IMDSv2’s PUT-then-GET authentication flow. Web applications vulnerable to SSRF typically cannot forge the complex PUT requests with custom headers required for token generation, significantly reducing the attack surface.
Implementation and Migration Strategies
Technical Implementation Requirements
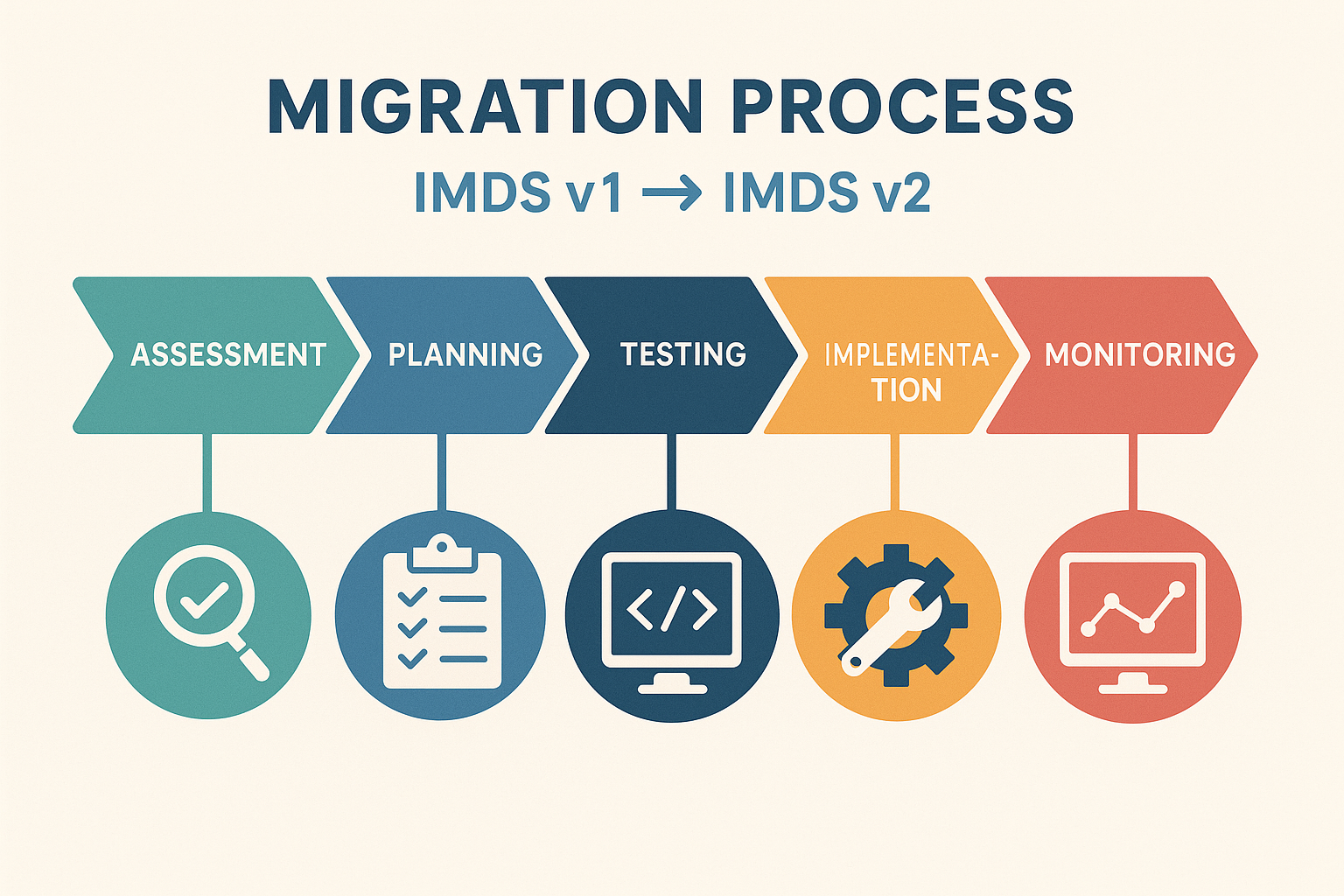
Migrating to IMDSv2 requires careful planning and coordination across development teams, as the transition involves updating application code, infrastructure templates, and deployment processes. Organizations must ensure their AWS SDKs and CLI tools meet minimum version requirements. These updated SDKs provide automatic IMDSv2 support, attempting the new protocol first and falling back to IMDSv1 only when necessary.
The implementation process typically begins with inventory and assessment of existing workloads. AWS provides tools to identify applications making IMDSv1 calls, enabling organizations to target their migration efforts effectively. CloudWatch metrics help track IMDSv1 usage across the environment, providing visibility into migration progress.
Infrastructure Configuration
Proper infrastructure configuration forms the foundation of successful IMDSv2 implementation. New EC2 instances can be configured to require IMDSv2 using launch templates, CloudFormation, or Terraform. For existing instances, administrators can use the AWS CLI to enforce IMDSv2 requirements.
Launch templates provide the most scalable approach for enforcing IMDSv2 across Auto Scaling groups and fleet deployments. The MetadataOptions block in infrastructure-as-code templates should specify HttpTokens as “required” and set an appropriate HttpPutResponseHopLimit. This configuration ensures that all instances launched from the template automatically enforce IMDSv2 requirements.
Migration Challenges and Solutions
Organizations implementing IMDSv2 frequently encounter several common challenges that require systematic approaches to resolve. Legacy applications represent the most significant hurdle, particularly those using older programming frameworks or third-party software that has not been updated to support token-based authentication.
Container environments present unique challenges for IMDSv2 migration. Multiple containers running on a single EC2 instance may access IMDS independently, making it difficult to track and update all usage patterns. Tools become particularly valuable in these scenarios, helping identify which containers are making IMDSv1 calls and require updates.
Migration Roadmap: Transitioning from IMDS v1 to IMDS v2
Performance considerations also influence migration strategies. Applications making frequent metadata requests may experience latency increases due to token management overhead. However, this impact can be minimized by implementing token caching strategies, where applications reuse tokens for their entire TTL period rather than requesting new tokens for each metadata operation.
Real-World Use Cases and Applications
Enterprise Security Transformations
Major organizations have documented their IMDSv2 migration experiences, providing valuable insights into real-world implementation challenges and benefits. Large-scale migrations demonstrate the scale and complexity of enterprise implementations. Their experience highlights the importance of phased rollouts and comprehensive testing before enforcing IMDSv2 across production environments.
The financial services sector has been particularly motivated to adopt IMDSv2 due to stringent regulatory requirements and the high value of protected data. Organizations in this space often implement IMDSv2 as part of broader compliance frameworks. The session-based authentication model provides auditable access controls that support compliance documentation and security assessments.
Microservices and Container Security
Container-based architectures benefit significantly from IMDSv2’s enhanced security model. In microservices environments, where multiple applications may run on the same EC2 instance, the token-based authentication provides better isolation and control over metadata access. Each containerized application must explicitly implement token management, making unauthorized access more difficult to achieve accidentally or maliciously.
Development teams have adapted their CI/CD pipelines to accommodate IMDSv2 requirements, implementing token management directly into deployment scripts and application initialization code. This integration ensures that applications can access required metadata while maintaining security boundaries between different components of the system.
Security Impact and Threat Mitigation
Protection Against Historical Attack Patterns
IMDSv2 directly addresses attack patterns that have been successfully exploited in real-world breaches. The Capital One incident of 2019 demonstrated how SSRF vulnerabilities in web application firewalls could be leveraged to access IMDS and steal credentials. IMDSv2’s token-based authentication would have prevented this specific attack vector, as the SSRF vulnerability could not have generated the required PUT request with appropriate headers.
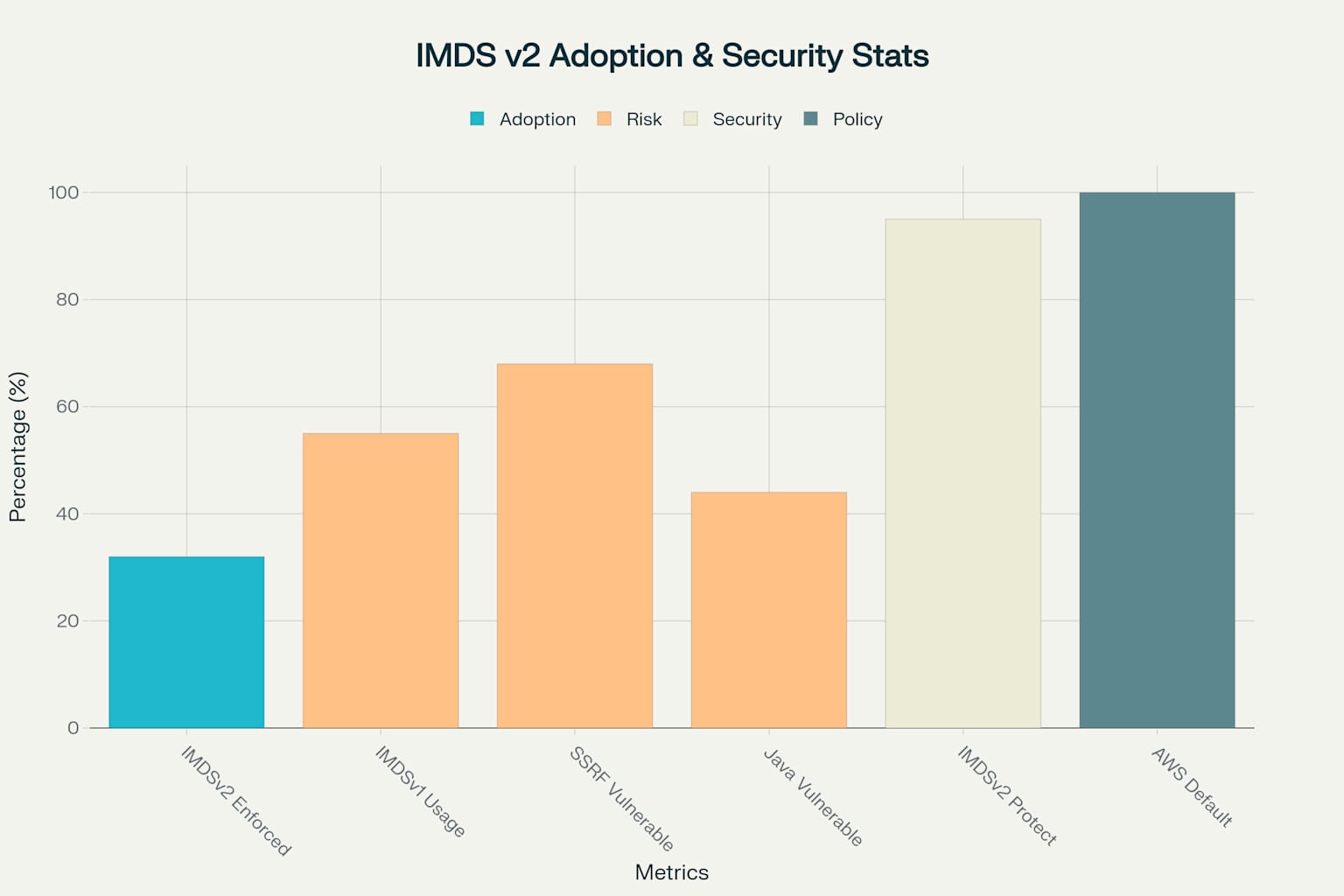
IMDS v2 Adoption and Security Statistics
Current statistics indicate that many organizations still have IMDSv1 actively configured, representing a significant ongoing risk. However, adoption is improving, with more organizations now enforcing IMDSv2 across their environments. AWS’s decision to make IMDSv2 the default for new instances has accelerated adoption rates.
Advanced Threat Protection
Beyond SSRF protection, IMDSv2 provides defense against sophisticated attack scenarios including container escape vulnerabilities and cross-tenant attacks. The instance-specific nature of session tokens prevents credential reuse across different compute resources, even when attackers gain access to token values. This design significantly complicates attack chains that rely on lateral movement between instances or services.
Side-channel attacks and timing-based vulnerabilities also face increased complexity under IMDSv2. The session management overhead introduces variability in response timing, making it more difficult for attackers to extract information through timing analysis. Additionally, the configurable token TTL allows organizations to limit exposure windows based on their specific risk tolerance and operational requirements.
Best Practices and Operational Excellence
Security Configuration Standards
Implementing IMDSv2 effectively requires adherence to established security configuration standards that have emerged from industry experience. Organizations should enforce IMDSv2 across all EC2 instances and disable IMDSv1 completely to realize the full security benefits. The hop limit should be set to 1 to prevent metadata responses from traveling beyond the instance boundary.
Monitoring and compliance verification represent critical ongoing requirements for IMDSv2 implementations. CloudWatch metrics provide visibility into metadata service usage patterns, enabling security teams to identify instances that may still be using IMDSv1. Regular compliance scans should verify that all instances meet organizational IMDSv2 requirements and identify any configuration drift.
Development and Deployment Integration
Modern development practices should incorporate IMDSv2 considerations from the earliest stages of application design. Development teams need training on token management patterns and error handling for token expiration scenarios. Testing frameworks should include IMDSv2 compatibility verification to prevent deployment of applications that cannot function with the enhanced security model.
Infrastructure-as-code templates must be updated to include IMDSv2 enforcement settings, ensuring that all newly deployed resources automatically implement the security requirements. Service Control Policies (SCPs) can provide organizational enforcement of IMDSv2 requirements, preventing the deployment of non-compliant instances.
Future Implications and Strategic Considerations
Industry-Wide Security Evolution
The introduction of IMDSv2 represents part of a broader industry trend toward zero-trust security models in cloud computing. As cloud providers continue to enhance their security offerings, the session-oriented authentication pattern established by IMDSv2 may influence the design of other cloud services and APIs. Organizations that adopt IMDSv2 early position themselves to benefit from future security enhancements that build upon this foundation.
Regulatory compliance frameworks are increasingly recognizing the importance of enhanced metadata service security. Standards bodies and industry regulators are beginning to reference IMDSv2 implementation as evidence of appropriate security controls. Organizations in regulated industries should consider IMDSv2 adoption as part of their broader compliance strategy rather than purely a technical security measure.
Cost-Benefit Analysis
While IMDSv2 implementation requires initial investment in application updates and staff training, the security benefits provide substantial return on investment through risk reduction. The prevention of even a single credential theft incident typically justifies the implementation costs many times over. Organizations should factor in not only direct security benefits but also compliance advantages and potential insurance premium reductions when evaluating IMDSv2 adoption.
Conclusion
AWS Instance Metadata Service Version 2 represents a paradigm shift in cloud security architecture, transforming a historically vulnerable service into a robust, defense-in-depth security control. The session-oriented authentication model addresses fundamental weaknesses in the original design while maintaining the operational benefits that make IMDS essential for modern cloud applications.
Organizations that have successfully implemented IMDSv2 report significant improvements in their security posture, with particular benefits in preventing SSRF-based attacks and improving credential protection. The migration process, while requiring careful planning and coordination, provides opportunities to modernize application architectures and security practices more broadly.
As cloud security threats continue to evolve, IMDSv2’s enhanced protection mechanisms position organizations to defend against both current and emerging attack vectors. The investment in IMDSv2 implementation pays dividends not only through immediate security improvements but also by establishing security practices and infrastructure patterns that support long-term cloud security objectives. Organizations that have not yet begun their IMDSv2 migration should prioritize this initiative as a fundamental component of their cloud security strategy.